Presenting the Sensitive Data Report
According to William Crowell’s famous quip, “the cybersecurity industry is a thousand points of light and no illumination.” And according to our new study, one of the darkest places in the entire field of security may be an employee’s downloads folder.
In fall 2022, Kolide partnered with Dimensional Research to survey IT, helpdesk, and security professionals about how their companies protect sensitive data–whether that’s private customer information, trade secrets, or the keys to the production environment. In particular, we asked what policies and tools they use to govern sensitive data once an employee downloads it onto their device.
We found that most companies have neither the appropriate policies to mitigate risk, nor the tools to enforce the policies they have.
The State of Sensitive Data
Let’s start with some highlights from the report:
- Only 46% of companies prohibit employees from downloading sensitive data onto their personal devices.
- Only 16% set limits on how long sensitive data can reside on an employee device.
- Only 37% can prevent devices that are in violation of sensitive data policies from further accessing sensitive data.
In other words, at most companies, employees can download sensitive data onto any device, keep it there for any length of time, and experience no consequences.
The seriousness of this comes into focus once you realize that these downloads happen all the time. The overwhelming majority of companies (83%) admit that their employees download sensitive data.
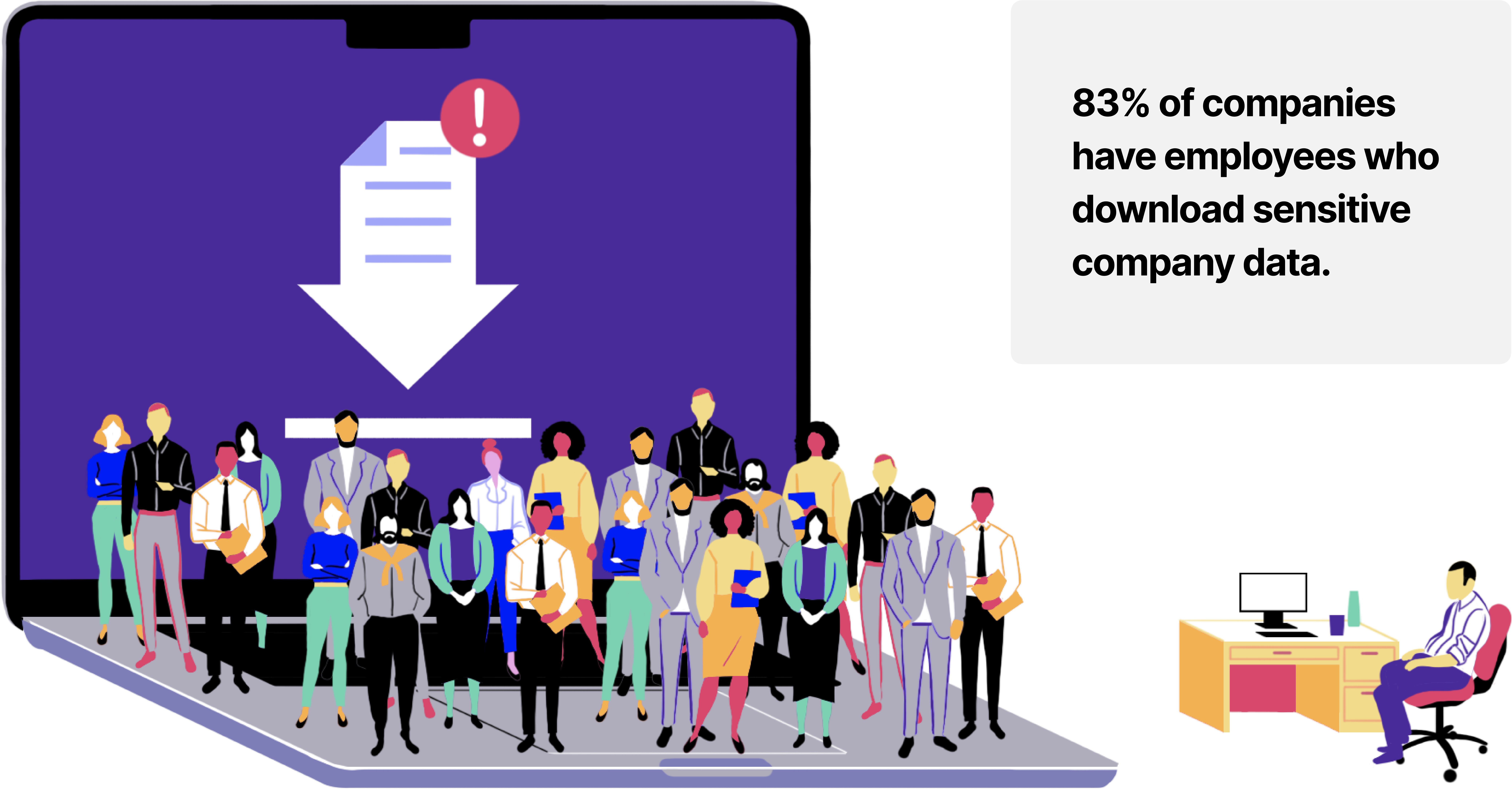
This doesn’t mean that 83% of companies are dropping the ball; it just means that employees have to download data to do their jobs. Banning that practice would be unfeasible–but doing nothing to manage it is extremely unsafe.
Most companies seem to have focused on authentication as the primary way of protecting data, but if devices aren’t secure, neither is authentication. The most dangerous type of sensitive data is the type that acts as the “keys to the kingdom” for a company’s systems–granting bad actors access to a company’s cloud apps or production environment. Yet only 38% of the professionals we surveyed had a policy against keeping plain-text access credentials on employee devices.
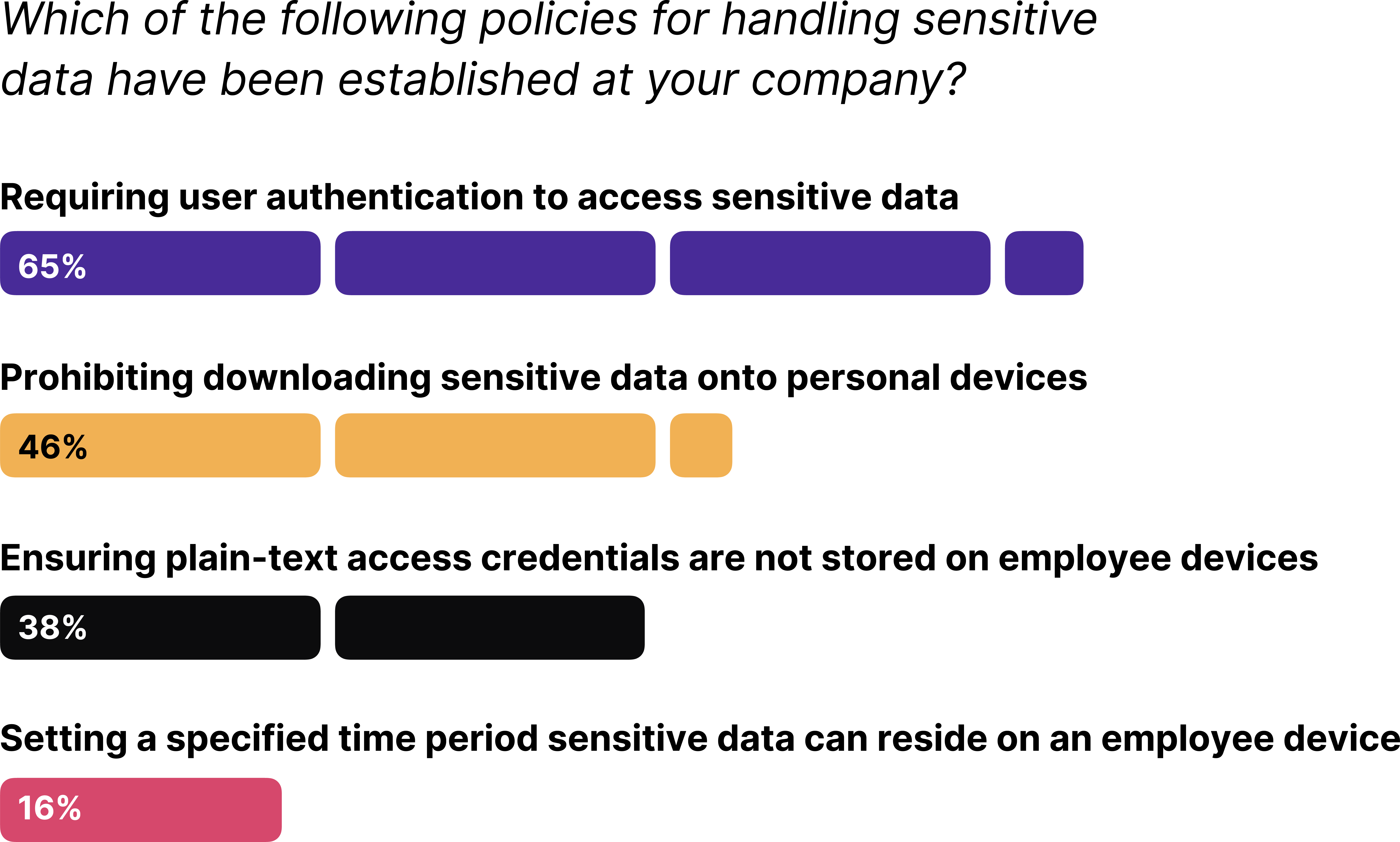
Keep in mind the graph above is only talking about policies, not having the means to enforce them. And even the best-intentioned policies don’t work without tools to back them up, since 91% of respondents report that their employees don’t comply with all sensitive data policies.
The C-Suite/Ground Floor Divide
One of this report’s most interesting findings is the large disparity in answers between executives and front-line workers. Executives confidently reported that they have policies and tools to manage sensitive data. But the people who work with those problems on a daily basis don’t share that confidence.
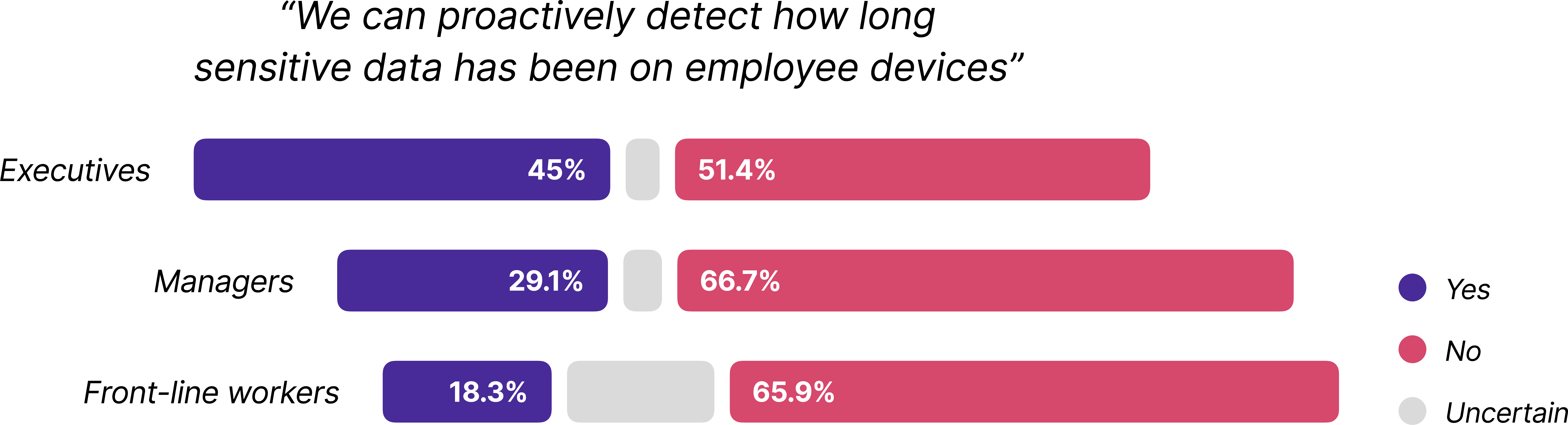
For example, look at the range of answers when we asked if their organization had an automated solution to detect how long sensitive data has been on employee devices.
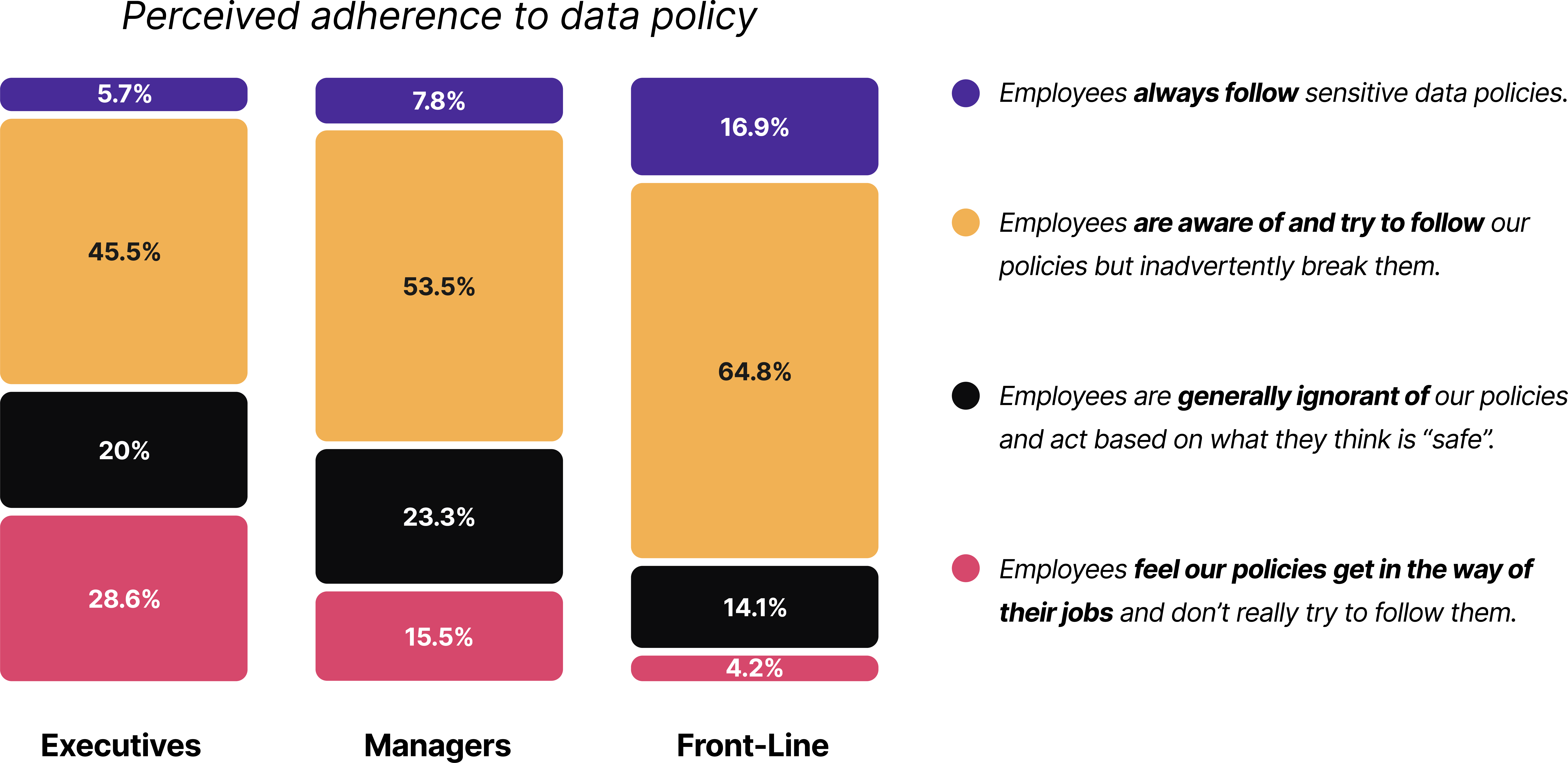
Another curious finding was that, while executives have a very high opinion of their tools, they regard their employees with suspicion. When we asked how well employees complied with data policies, 28.6% of managers said their employees “feel our policies get in the way of their jobs and don’t really try to follow them.” Only 4.2% of front-line workers shared that dim view.
The data itself doesn’t tell us why opinions vary so much depending on where you are in the org chart. However, one explanation might be that executives are there for the sales pitch in which security companies promise them the world, but front-line workers are the ones who encounter the limitations of those tools. For example, many device management solutions claim that they can automatically perform OS updates across a fleet. But in practice, that means they have to force restarts on users. It’s disruptive and unpopular, so IT teams tend not to go that route, which means the problem remains unsolved, even though executives consider it dealt with.
By the same token, executives may be exposed to a “scare tactics” version of Zero Trust security that treats end users as threats. But the IT and helpdesk teams who work with users daily see them as fallible rather than feckless.
Device Compliance is the Missing Piece of Zero Trust
The results of our survey are significant and sobering, but they are not intended to be scolding. We recognize that the majority of respondents haven’t solved the sensitive data problem because they haven’t had the tools to do so.
MDMs have limited capabilities to get devices in a secure state. On the other end of the spectrum, Data Loss Prevention (DLP) tools are too intrusive for most companies–workers are surveilled rather than educated.
Kolide is interested in these questions because we see ourselves as the Goldilocks solution to the sensitive data problem. Here’s how it works: IT admins use Kolide to run queries for specific types of data (as opposed to the invasive method of hoovering it all up), and our agent proactively flags devices that are out of compliance. Then, the next time a user logs into their cloud apps, we inform them of the problem and give them instructions to fix it.
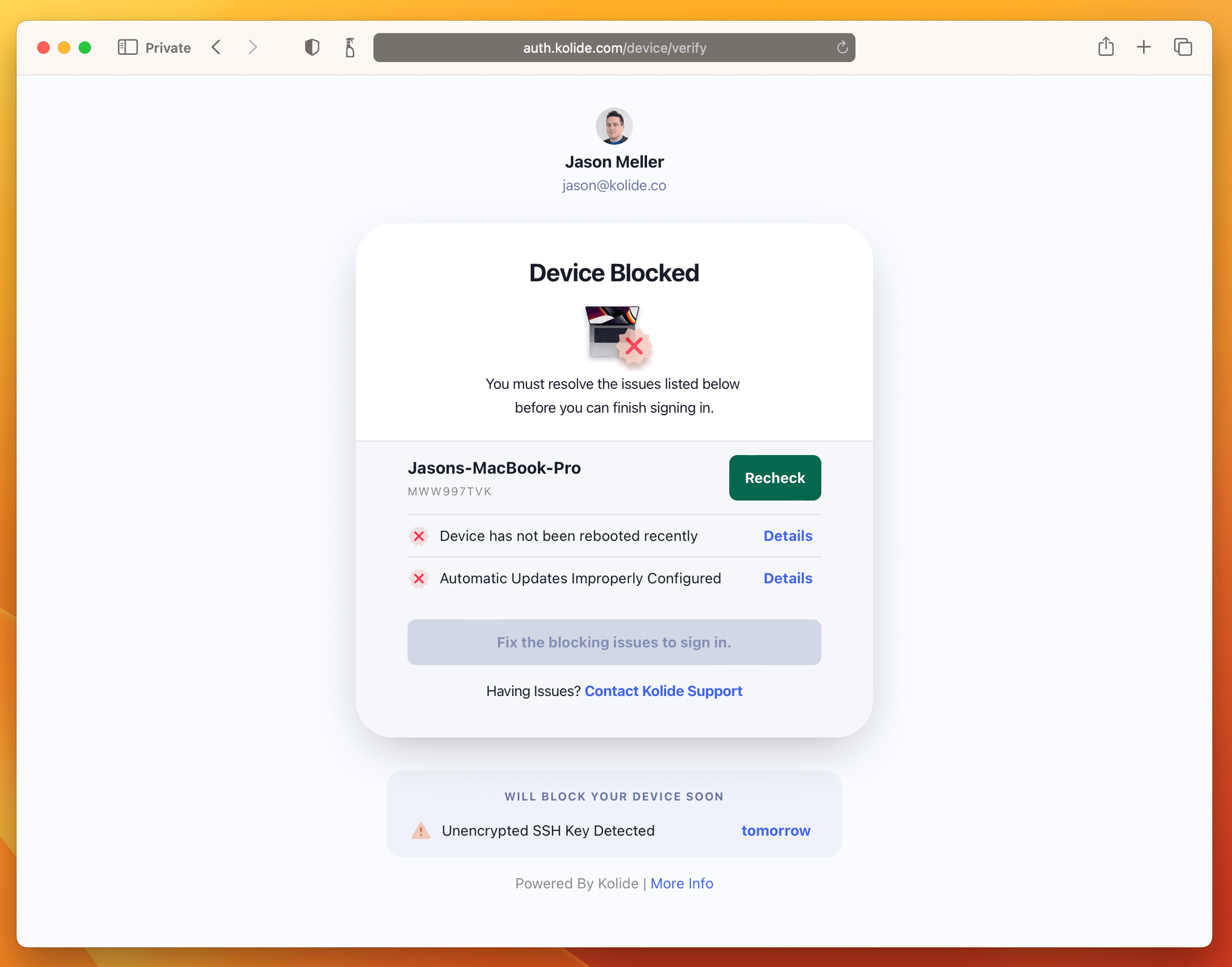
For example, if an engineer has a debug log in their downloads folder for 60 days, Kolide will prevent them from logging in until they’ve deleted it. It’s an approach that gets to the heart of what we learned from the report: that end users are human beings who generally want to do the right thing but need communication and (sometimes) consequences.
Without further ado, we’ll leave you to the report itself, which contains many more granular and surprising insights.
So what are you waiting for? It’s free! We don’t even make you sign up for the newsletter! (But if you’ve read this far, you really should sign up for the newsletter, because you clearly care about this stuff as much as we do.)





