
How to Find and Securely Store 1Password Emergency Kits
1Password Emergency Kits usually contain the account's secret key and maybe even the master password. It's important that they are secured.
What Is a 1Password Emergency Kit?
1Password is a popular password manager used by both end-users and enterprises that encourages good password hygiene and safe-storage practices.
The general premise is instead of juggling multiple passwords, users only need to remember a single master password to unlock a vault containing individual passwords that are generated for each service they use. Since generated passwords don’t need to be memorized, they can be more complex and radically different for each service. If one service gets compromised and the password is leaked, the damage a bad actor can do is only limited to that one service.
When you create a 1Password account, you need to create and remember the master password, but if you want to set up the account on a new device, you also need something called the secret key.
The Secret Key
The secret key is an additional random alpha-numeric password generated automatically by the 1Password app when creating a new account. The secret key is specific to your account, and it must be entered by you when you set up your account on another computer (or when you sign in via the web client).
No one else knows your secret key but you (including 1Password), and without it, you cannot sign in to your account.
The Master Password
Unlike the Secret Key, the Master Password is intended to be a complex but memorable password you will need to enter often to access your account. It should be written down on a physical piece of paper and stored in a secure location (e.g., a physical vault or safe deposit box).
The 1Password Emergency Kit actually has a place to write the Master Password. While yes, you can write it there, an even better approach is to keep the password and the emergency kit separated physically in two distinct secure locations.
If you lose either the secret key or the master password, regaining access to your 1Password account can be extremely difficult (if not impossible). 1Password generates an emergency kit that users can securely store to prevent this outcome. This emergency kit can help them recover their account should they lose or forget these key pieces of data.
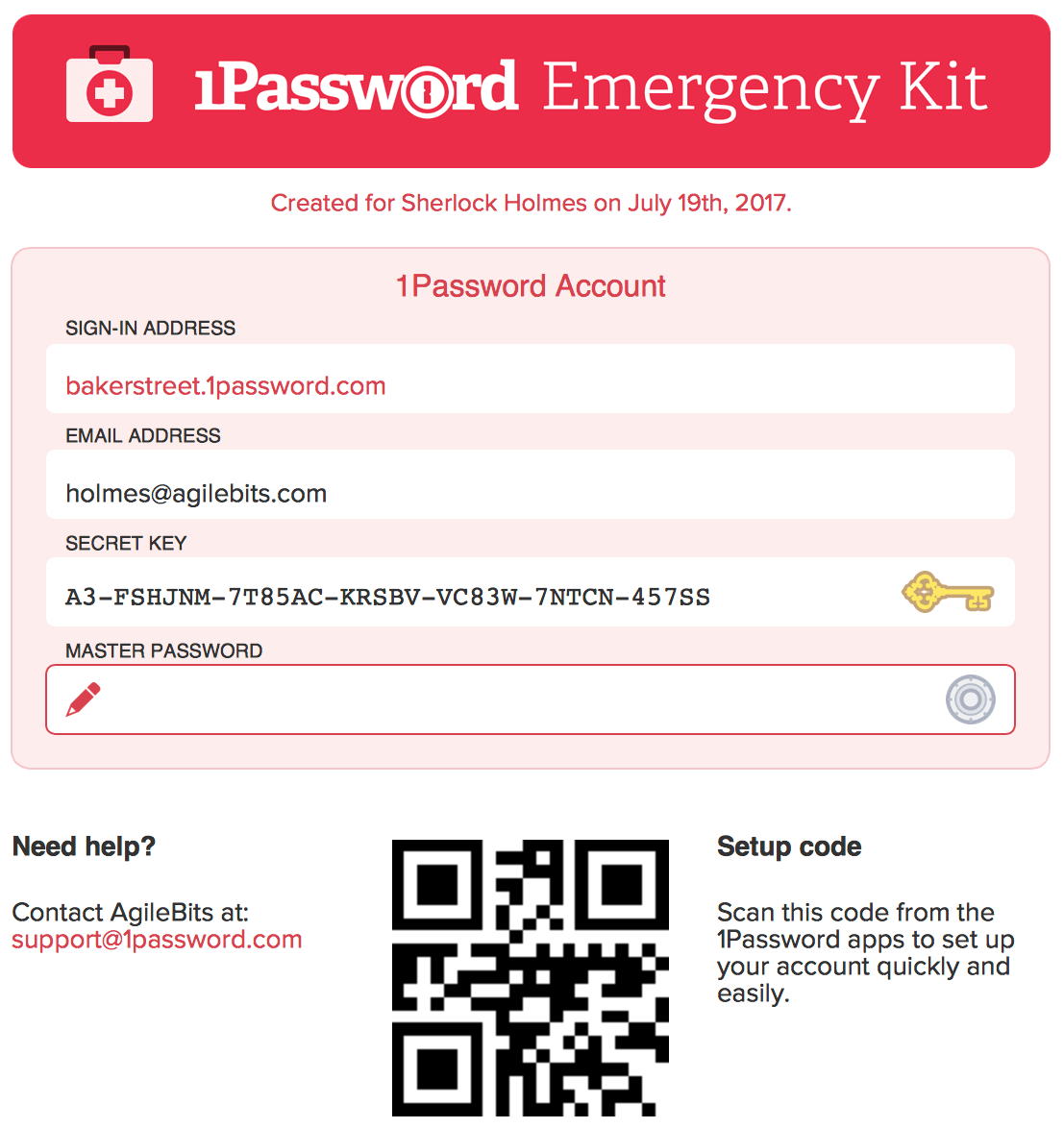
Using this, you can re-gain access to your 1Password accounts by following the prompts. All details except the Master Password are automatically filled in when the emergency kit is generated.
How Does a 1Password Emergency Kit End Up on Disk?
During the setup process, 1Password enables users to download the emergency kit right from their web browser so that they can fill it out later.
Since this step often occurs in a web browser context, it’s common for them to be downloaded to the default Downloads location or other user folders like the Desktop.
1Password recommends moving the emergency kit file to a USB thumb drive or printing the document and putting it in a safe place like a deposit box, but this step is often missed or skipped. As a result, most people download it, keep it in their default Downloads folder and forget it until they need it.
Is Keeping a 1Password Emergency Kit on Disk Actually Dangerous?
Leaving a 1Password Emergency Kit on disk severely weakens the additional security 1Password provides, especially when it comes to the security of the secret key.
Imagine a bad actor can obtain one of these kits. Even in the best-case scenario – the user didn’t write the master password inside - the bad actor still has nearly all the information they need to access the account.
Having the master password be a single point of failure, preventing the worst-case scenario (a user’s personal and company accounts being completely compromised) is a very precarious position.
This is a classic low-probability / high-impact risk, but given the steps to secure these files should only take a few minutes, we feel it’s well worth getting them off the device whenever possible.
How Should I Securely Store a 1Password Emergency Kit?
According to the 1Password’s support site, the best option is to print the kit, and keep it in a secure location, like where you keep a passport or birth certificate.
If you are using 1Password for Teams through your organization (and don’t have a separate vault for personal passwords) and printing the kit is not feasible, consider if you need the emergency kit at all? In most cases, an IT administrator can help you recover access to your company’s account even if you don’t know the secret key and your master password.
How Do I Find 1Password Emergency Kits on My Devices?
It can be tricky to locate these files accurately, especially since they can be potentially located anywhere on the device.
One reliable method on macOS is to use the full-text search capability in Spotlight to lookup files by a phrase found in every emergency kit. We can also match off the file name.
We can construct a spotlight search in the terminal using the utility mdfind:
mdfind \
"kMDItemTextContent = 'sign in to your 1Password account in an emergency' ||
kMDItemFSName = '1Password Emergency Kit*.pdf'
If any files are present on the system, they will be output to stdout. On
Windows and Linux, finding files this way is impossible, and other less
performant, full-disk recursive search utilities like ag, find, and grep
will need to be utilized if a non-indexed search utility isn’t available. Another
approach can be to tap into the download history maintained by the various web
browsers.
How Does Kolide’s Detection Work?
Kolide extends osquery with its endpoint agent to help locate these files across Mac, Windows, and Linux devices using on-device detection, which doesn’t require reading the contents of files or sending private information like your user’s browser history to Kolide.
For example, on macOS, Kolide can use osquery to leverage Spotlight and find files based on the text inside the file.
On Windows and Linux, Kolide can use osquery’s file table in conjunction with automatically constructed tables based on the various web browsers’ download histories.
This approach would allow for near-perfect accuracy even if the file were moved or renamed while preserving privacy (all detection is done on the client).
How Does Kolide Remediate This Problem?
This problem cannot be remediated through traditional automation with tools like an MDM. You need to be able to stop devices that fail this check form authenticating to your SaaS apps and then give end-users precise instructions on how to unblock their device.
Kolide's Okta Integration does exactly that. Onece integrated in your sign-in flow, Kolide will automatically associate devices with your users' Okta identities. From there, it can block any device that exhibits this problem and then provide the user, step-by-step instructions on how to fix it. Once fixed, Kolide immediately unblocks their device. Watch a demo to find out more.
