The Security and IT Admin's Guide to macOS Ventura
The release of macOS Ventura is generating plenty of excitement–Apple’s marketing juggernaut has done a great job of convincing users that they need to install Ventura immediately. Not that Apple has overdone the hype; they’ve got a lot to be proud of with this release.
Still, this situation puts IT admins in an unenviable situation, because it’s their job to ensure the stability of their org’s IT environment. And stability, sadly, doesn’t play well with excitement.
So what’s an IT admin to do? Well, since you can’t keep end users from updating, (although you can delay it for a few months) you need to get up to speed on what this update brings, so you can support it on day one.
So far, the most talked-about changes are:
The Continuity Camera that lets you use your iPhone as a webcam. Opinion on that one seems to be divided between “ain’t it cool” and “why didn’t they just design a better built-in webcam in the first place?” Regardless, IT pros should prepare to get a lot of reimbursement requests for camera mounts in the coming weeks.
Stage Manager which is supposed to help users focus on one app at a time and keep the desktop better organized. (To which the ADHD community says “game on.”)
System Settings is replacing System Preferences, which had become unwieldy in recent years. The new design brings it more in line with the iOS experience, which is also a trend we see in several other Ventura changes. The beta version of System Settings was riddled with bugs, but as our founder noted on Twitter, those mostly seem to be resolved.
I am happy to report that MANY of things mentioned in this thread are completely fixed or much better.
— Jason Meller (@jmeller) October 24, 2022
Is the new macOS Ventura System Settings app perfect? No but that wasn’t expected.
Is it orders of magnitude better than the betas? Oh yeah.
Thanks Apple for working so hard. https://t.co/EG42Fhl2LX
Each of these features will undoubtedly get thousands of words written about it, but here, we’re going to focus on Ventura’s security changes, and particularly what they will mean for IT admins and security professionals.
There’s a lot to talk about–from a security perspective Ventura has some of the most significant updates in years. And while it’s anyone’s guess whether we’ll all be using the Desk View camera in a few years, changes like Passkeys and Rapid Security Response are going to have a big impact for the foreseeable future.
So let’s take a bite of the Apple! go on an adVentura!
read about these new features.
Passkeys
The arrival of passwordless authentication for the masses is easily the most consequential change in Ventura. It’s also the one we’re going to spend the least amount of time on, since we devoted an entire article to how they work and their broader implications.
Passkeys have already made their debut on iOS 16, but so far, only a handful of apps have enabled them. The big early adopters of passkeys probably won’t be in the consumer and mobile-first world, because consumers are already accustomed to the ubiquity and ease of Sign in with Apple. Neither eBay nor Kayak, for example, prompt you to create a passkey during account creation; you have to activate it yourself under “settings,” which most users won’t do on their own.
But the debut of passkeys on Ventura is far more significant than on iOS, because passkeys deliver the most up-front value not to consumers but to enterprises looking to do away with traditional passwords. Passkeys solve many of the challenges associated with the single-device security keys browsers can currently generate, including credential backup & recovery, cross-device usage, and sharing.
These multi-device benefits will begin to become obvious with the launch of macOS Ventura, which will allow your Mac to use passkeys generated on your phone (and vice versa).
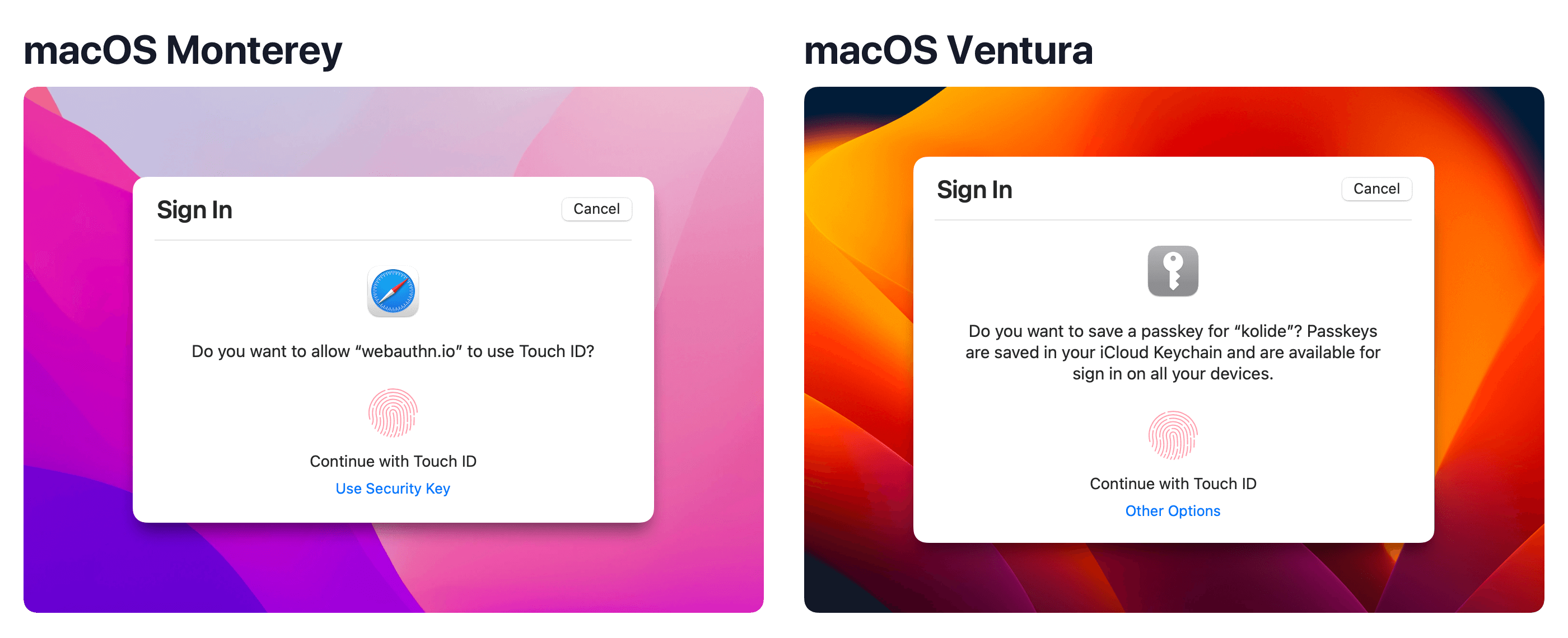
While Apple is primarily marketing passkeys to consumers, its true value will be realized by technology builders, who will no longer have to worry about the messiness of passwords. Companies will likely begin this transformation for their workforce, and eventually, for their customers. So if your organization relies on browser Webauthn for certain kinds of authentication, it’s time to start paying attention.
From Apple’s WWDC presentation about Passkeys
“…Passkeys are replacing Safari’s legacy platform authenticator. Existing credentials will still work and still be bound to the device they were created on, but new platform credentials will be created as passkeys. They can be differentiated from legacy credentials during registration, as passkeys will not provide an attestation statement.”
This means if you have an WebAuthn system that allows users to self-register, Multi-device Passkeys will be generated if the end-user registers their credential in the Safari browser. This process can break if you require an attestation statement which is no longer needed for Passkeys.
Despite the inevitable headaches that come with such a change, this should be cause for celebration. Unlike the device-bound credentials that were supported previously, Passkeys can be recovered by end-users if they are lost, transferred to other devices, and even sent to others via Airdrop when the person is in close proximity. These sharing security features also work when users attempt to use Passkeys in non-Apple devices and browsers, like ChromeOS.
IT admins and security teams should be rooting for the success of passkeys, since weak and compromised passwords have been at the root of many a data breach, and the WebAuthn standard is a huge step forward for security. But it’ll take time, widespread commitment to implementation, and the participation of Microsoft and Google to make passkeys a success.
So what’s an IT admin to do? Well, since you can’t keep end users from updating (although you can delay it for a few months), you need to get up to speed on what this update brings, so you can support it on day one.
Rapid Security Responses (RSR)
Ventura is also introducing RSR, which allows Apple to ship important security updates to macOS much faster than before.
Previously, shipping even trivial security fixes involved releasing large multi-gigabyte
updates, which were necessary to preserve the cryptographic integrity of the OS.
With RSR, Apple can take advantages of newer technologies like cryptex and the dyld
shared cache to package updates that are a fraction of the size.
This simplified process means much faster downloads for users and a patching process that is much more reliable. In fact, it’s the same system already in place and used by millions on iOS and iPadOS.
Still, questions remain about RSR. For one thing, it’s not clear what types of patches they’ll be capable of. As Eclectic Light writes:
“What remains to be seen is whether Apple also uses RSR to promulgate patches for more severe bugs in macOS. Although this may be possible for some, the most severe are generally considered to include Mach zone memory leaks and other bugs likely to lead to kernel panics, which will still probably require a formal macOS update.”
The other concern–at least for security professionals–is how to ensure users have RSR enabled. The setting is enabled by default, but admins will still need ways to ensure it stays that way. (Naturally, that’s something we’re thinking about here, since checking that end-users have enabled automatic updates is among our most important features.)
Contrary to some pre-launch reporting, RSR will still require reboots and user approval. Apple writes:
“Rapid Security Responses don’t adhere to the managed software update delay; however, because they apply only to the latest minor operating system version, if that minor operating system update is delayed, the response is also effectively delayed.”
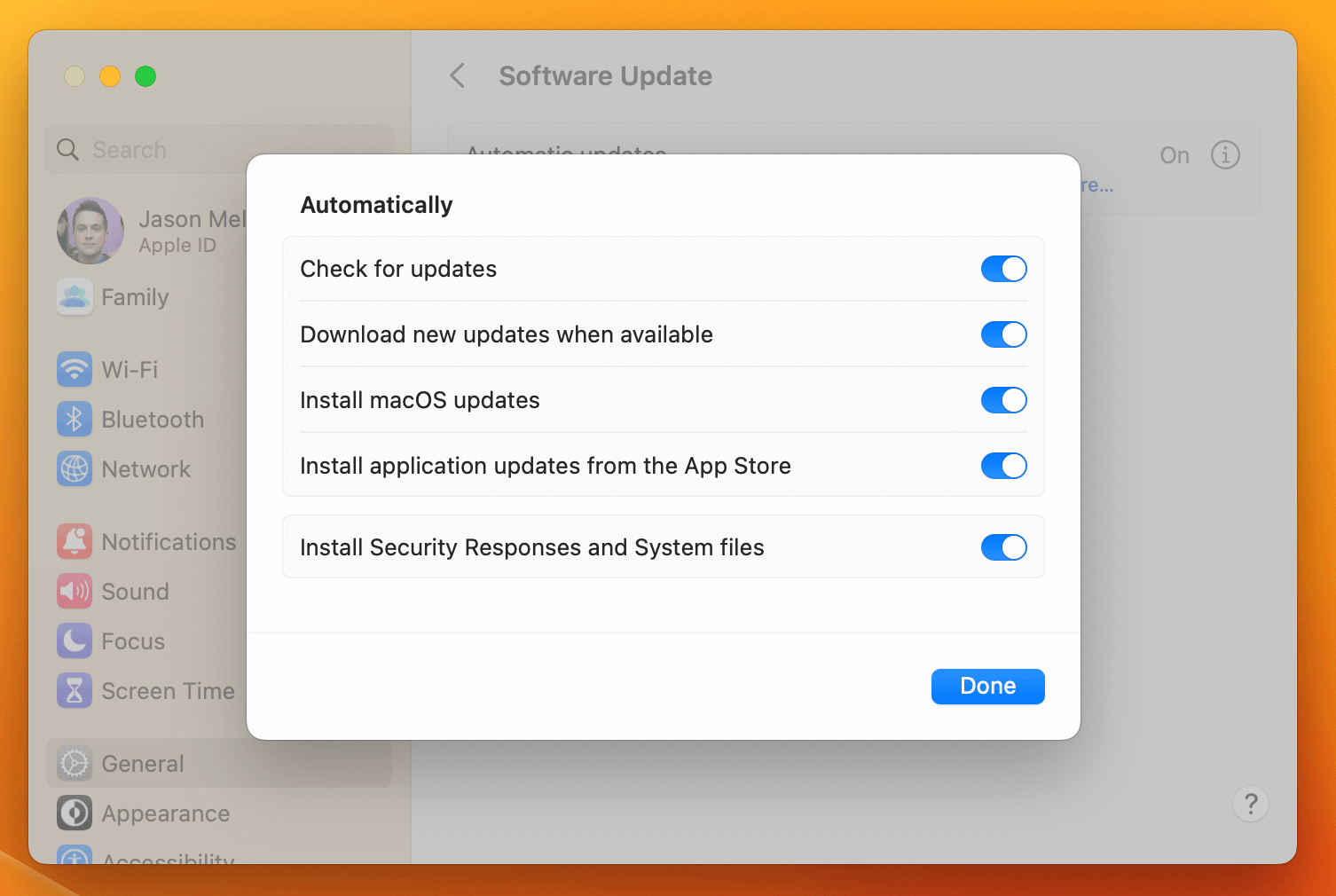
Apple’s documentation offers some guidance on how to manage RSR via MDM, but we’ll wait to see whether it makes a meaningful impact to the lives of Mac Admins
Gatekeeper and Notarization
For years, Gatekeeper has been the keystone of macOS security, working in tandem with File Quarantine and XProtect to fight malware via a “scan at launch” approach. (We wrote an entire article on Gatekeeper, which is really a fascinating tale about Apple’s evolving approach to malware.)
sudo spctl --master-disable command.
Gatekeeper’s role has traditionally been to check an app’s notarization and code signatures while it’s in quarantine; once it’s out of quarantine Gatekeeper essentially treats it as trusted. The problem with that is it leaves apps vulnerable to malicious exploits that modify apps once they’re out of quarantine.
Ventura attempts to solve this problem by having Gatekeeper run signature and notarization checks every time an app is run. That will significantly improve Gatekeeper’s anti-malware capabilities, but it also introduces issues if an app has been modified by the user or during an update.
Eclectic Light has (another) great explainer on this, and calls out the potential problems for developers. “Many apps distributed outside the App Store incorporate a mechanism, commonly using Sparkle, to update them in place. In some older cases, that leaves the updated app with discrepancies in its code signing and/or notarization.”
When this happens, the simplest route for users will be to simply uninstall their copy of the app and replace it with the latest version.
Crucially, this will not impact unnotarized apps, so users can still run open-source and homemade software, with the same degree of freedom and risk that entails.
Lockdown Mode
One of Ventura’s splashiest security features is Lockdown Mode, despite the fact that it’s really only designed for a small subset of users.
Per Apple:
“Lockdown Mode is an optional, extreme protection that’s designed for the very few individuals who, because of who they are or what they do, might be personally targeted by some of the most sophisticated digital threats.”
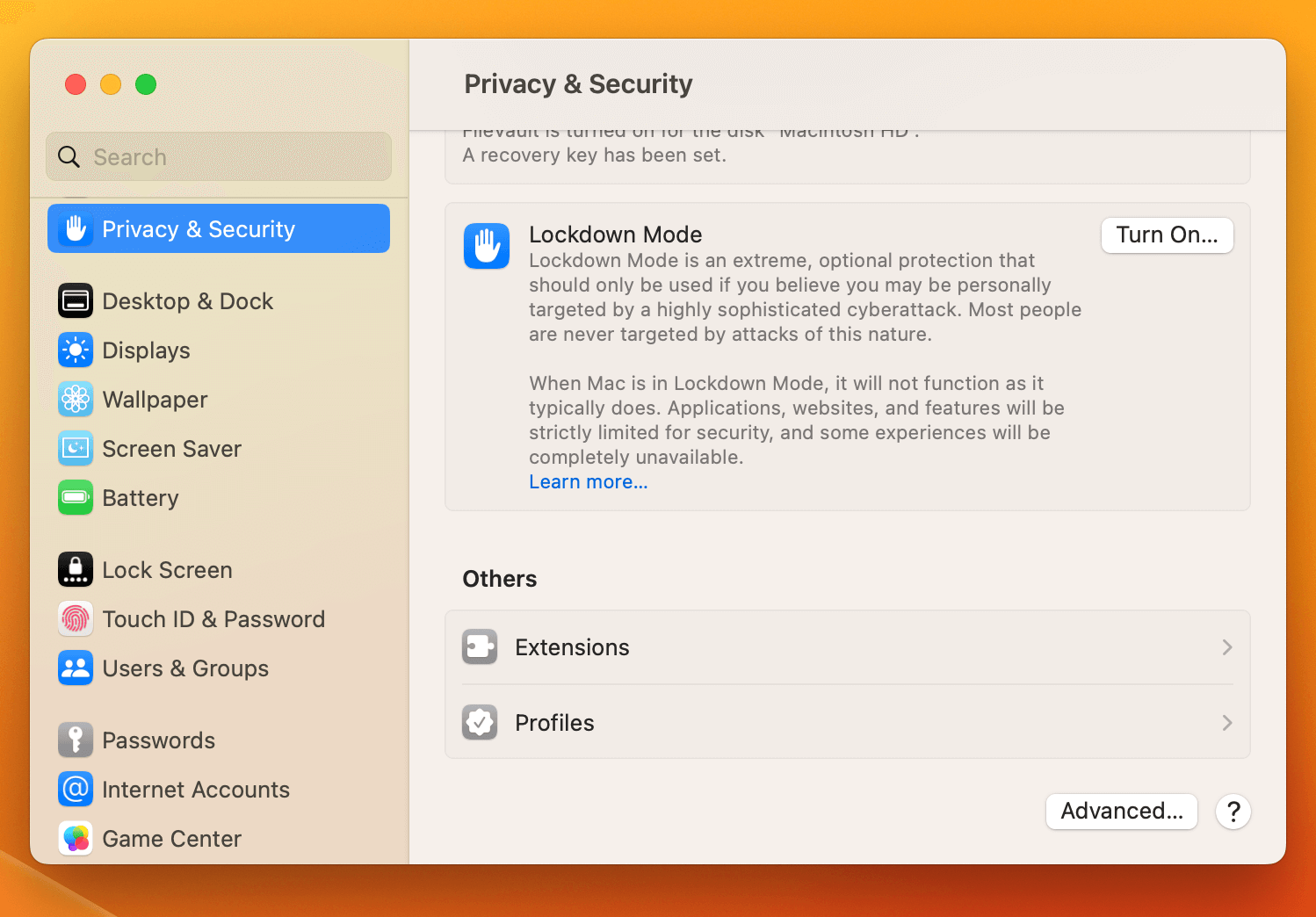
When a user enables Lockdown Mode, it changes how the device behaves in a number of ways, such as:
Blocking FaceTime calls from unknown numbers
Blocking most message attachments, including links
Preventing configuration profiles from being installed, and from the device being enrolled in MDM
USB accessories won’t connect unless the device is unlocked (this one probably has the most real-world usefulness, for when a device with sensitive data is in an unsecured physical environment, and can be enabled separately as Accessory Security)
Today I tested #macOS Ventura (beta) in Lockdown Mode to see what breaks: https://t.co/P6zxBjC7EJ
— Thomas Strömberg (@thomrstrom) October 3, 2022
✅ Works: Chrome, Docker, Go, Homebrew, Kolide, Lima, minikube, osquery, Slack, ssh, Yubikeys, VS Code
❌ Doesn’t work: VirtualBox (Extension blocked)
Verdict: Looks great!👍 pic.twitter.com/N08fXLzoav
For IT admins who worry that employees could use this feature to evade MDM, Apple assures us that devices that are already enrolled before Lockdown Mode is turned on will remain manageable.
But Apple also cautions against overzealous security teams who’d love to enable this for every Mac in the fleet. They write: “Lockdown Mode is not a configurable option for Mobile Device Management by system administrators, as it’s designed for the very small number of individual users who might be targeted by extreme cyber attacks.”
Most users will never need this feature, but it’s a powerful gesture that shows how seriously Apple takes its commitment to privacy, and the people who do need it will be glad to have it.
Closing Thoughts
Ventura is brand new, and we’ll learn more about each of these features once they’re out in the world. But if first impressions are anything to go on, this iteration of macOS cements Apple’s brand as a security leader. As Apple knows all too well, you can’t please everyone, but this release might just make everyone a little safer.
Want to stay up-to-date on endpoint security news like this? Sign up for our biweekly newsletter!





